|
|
| Line 48: |
Line 48: |
| | *[[Apps and Tools]] | | *[[Apps and Tools]] |
| | *[[Privacy Protection]] | | *[[Privacy Protection]] |
| | + | *[[To encrypt or not to encrypt]] |
| | + | *[[Networks under certain circumstances]] |
| | <hr class=simpleline> | | <hr class=simpleline> |
| | | | |
| Line 53: |
Line 55: |
| | '''Handbook''' | | '''Handbook''' |
| | [[File:Travel guide.png | 250px | link=http://www.gp-digital.org/publication/travel-guide-to-the-digital-world/]] | | [[File:Travel guide.png | 250px | link=http://www.gp-digital.org/publication/travel-guide-to-the-digital-world/]] |
| | + | |
| | ===Travel Guide to the Digital World=== | | ===Travel Guide to the Digital World=== |
| | [http://www.gp-digital.org/publication/travel-guide-to-the-digital-world/ Download] | | [http://www.gp-digital.org/publication/travel-guide-to-the-digital-world/ Download] |
| | </div> | | </div> |
| | </div> | | </div> |
Revision as of 18:50, 11 February 2022
It is surprising easy to encrypt emails - and more and more it is demanded. Think not only about your needs. When you send personal data from participants in your project like addresses or motivation letters, are you really sure, that there is no implication for them?
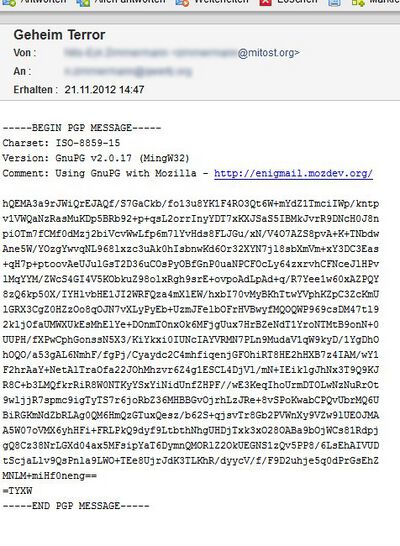
How does it look?
In the example to the right you see, how such a message is looking like for not authorised readers. It is a text-only message with encrypted information between the start and end tags for PGP.
How to use it?
From version 78 the popular open source email program Thunderbird includes Open PGP and S/MIME encryption technology. To use PGP encryption, you and your communication partner have to install both an encription program based on the standard PGP. PGP stands for 'pretty good privacy'. After installation you generate your personal key. How to use it: Step-by-step explanation.
Find here an overview over other software and providers supporting Open PGP.
The idea: public and private keys
Every user of PGP has a private and a public key.
|
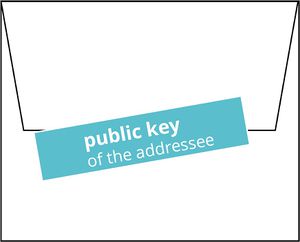
The public key is used by another person, that wants you to send a message for encrypting.
|
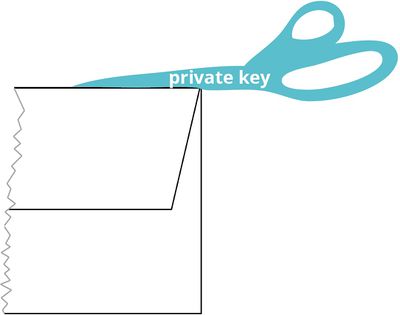
The private key should be kept secret: It is used only by you to decript encrypted messages of another person to you.
|
Key Management

 nez
nez
Related:
Also interesting:
Handbook

Travel Guide to the Digital World
Download