We were able to copy and paste mass entries from databases, automatically collecting numbers and email addresses of people we were in contact with and sending around emails to hundreds of recipients. Over time we forgot how to remember a telephone number. As the Internet started connecting all our devices and the smartphone became our central communication management tool, new opportunities were opened. Our notebook might now be migrated into a cloud which means, technically, from a client computer to a server, and can now be accessed through many different devices. It has become independent from the material place of storage which relieves us from fearing its physical loss. If your mobile phone is broken or stolen, access your notes or addresses from your cloud space simply by using a new device.
Contents
The Evolutionary Pattern of Digitization
- Analogue practices undergo a digitization
- Digitized devices and services link to others. New devices beyond the server or desktop computer appear.
- Linkage and networking of devices, services and data in digital processes (recoding, extracting, comparing, monitoring or analysis of data) enable new forms and business models.
Digitalisation draws its dynamics in particular out of the opportunities of the latter two.
Ubiquitous Computing
The coexistence of more and more apps and of more and more devices around us is putting the vision of ubiquitous computing into reality. Digitalisation pioneer Mark Weiser postulated in 1991, that a lot of our devices today would be more or less “invisible in fact as well as in metaphor” (Weiser, 1991). Our devices are small and intuitive, and we don’t even recognize them as computers. Their value lies on the one hand in their small size and intuitiveness, but their impact is their connection to servers, to other systems or to data processing. In an Internet of Everything, the machine is embedded in our social context and so are intelligent plug sockets, fridges, automotive body computer modules, factory robots, or home media centres. Also wearables (and even some implants) have “become social actors in a networked environment” (Spiekermann, 2010, p. 2).
Internet of Everything: Computed devices for different purposes, of different sizes and with different abilities interact with other devices (Internet of Things), and with the surrounding space through our facility-installed technology (Smart Home), and the social environment.
Ubiquitous Computing: A technological vision of many, often small, and very differently connected computing devices, deeply embedded in our daily routines, interacting intuitively with us and with each other.
“The real power of the concept comes not from any one of these devices; it emerges from the interaction of all of them” (Weiser, 1991, p. 98). Digital assistants like Amazon’s Alexa, Google Assistant and Samsung’s Bixby are good examples that have brought ubiquitous home computing to a new scale: They are always on and monitoring their environment including the beings around them, communicating independently with the services behind them. We no longer experience “stupid” machines that sense environmental data and send it to other machines. More and more, they actively accompany us. We can also phrase it as such: the price for intuitive and individualised computing is reliance on external infrastructure – and also interception.
Datafication
Necessary for the implementation of this vision are platforms: „Digital infrastructures that facilitate and shape personalised interactions among endusers and complementers, organised through the systematic collection, algorithmic processing, monetisation, and circulation of data.“ (Poell et al., 2019, p. 3).
Algorithm:A set of computational rules and steps proceeding data with the purpose of extracting information out of it or triggering action.
Platforms: Digital infrastructures that facilitate and shape personalised interactions among endusers and complementers, organised through the systematic collection, algorithmic processing, monetisation, and circulation of data.“ (Poell et al., 2019, p. 3)
Datafication: extracting personal data from user interaction, processing it digitally and turning it into (added) value.
With growing “smartness” the amount of data and the server capacity of platforms grows, which is needed to process all the data and manage cloud spaces. It is also now possible to merge different kinds of data. Although formerly, shopping data and other household expenses like rent, gas/water/electricity and bank transfers would have been documented in a household book, digitalisation’s strength is that they may be merged digitally: Users not only gain a better overview but also a clearer picture. Thanks to built-in analysis and evaluation functions these devices also create new data through their usage (such as metrics, location data, and metadata), allowing better analysis (for example, from where and how often somebody accessed their notes) or by attaching data to specific persons. For instance, a digital picture stores the copyright holder, the date and location it was taken and the camera information. In order to find out if somebody was in summer 2020 in fact in Spain, we could simply collate data from credit card bookings, uploaded images (with the metadata), or social media posts.
Datafication: extracting personal data from user interaction, processing it digitally and turning it into (added) value.
Tracking:Recording personal data constantly over a certain time period and drawing information out of it.Source: EU-FRA 2020-2
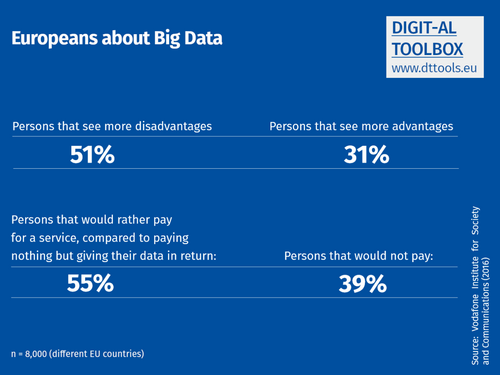
But how to make sense out of all the data? The more distinct information we have, the less an individual is able to process it. Now “big data” comes into play. This term describes an automated method of gaining insight on the basis of quantitative data by building statistical correlations and relations between a variety of data types using a massive amount of data. Big data could help users to draw new conclusions – and also the owner of the big data servers and algorithms, the platforms, to draw conclusions about their customer(s).
Big Data: Method of gaining insight on the basis of quantitative data by building statistical correlations and relations (between a variety of data types and a massive amount of data). Facilitated by algorithmic computing. Via modelling social reality through statistical approximation, the fundamental aim of big data is to forecast human behaviour, to understand societal processes, or to influence human activities.
Even the analysis of different data which seems not to be in logical relation to each other might lead to valuable insights. If data from other persons were also to be available, this would be even better. For instance, could an analysis software conclude: “Bulgarian males between 30 and 40 spend usually many time in the later evening in social networks. They also buy more frequent cookbooks.“ Maybe, this is not very interesting or valuable for the concrete user person, but it definitely is for the marketing of cooking books. By processing different data, like information on nationality, gender, book sales and individual social network time, big data is modelling social reality through statistical approximation (Mayer-Schönberger, 2015). This leads to the ability to forecast human behaviour (the user may be a cookbook buyer and might also hear Death Metal) or to understand societal processes (at places in Bulgaria with many cookbook buyers were many demonstrations), or even to intervene in these (if you give Bulgarians desert cookbooks for free, or are organising Death Metal concerts, they are less frequently going on protests). An analogous forerunner of this way of thinking is perhaps the scoring of a person‘s creditworthiness, which is often consulted when credit decisions are made, or for rentals. Here, too, very different data are brought together. Information that is generally available – such as place of residence, gender or age – is combined with experiential data – such as payment discipline in certain neighbourhoods, in age groups or among genders. In addition, personal data helps to narrow down this general picture more precisely, such as one‘s own payment behaviour, family situation or profession.
The example from online commerce also makes us think about how attractive this type of data processing can be and already is in very different application areas. Data of many people or many data of one individual can help insurance companies to calculate or even control their risks. Retailers can tailor their offers and customer service. Human activity can be analysed and controlled more precisely, for example at work, in traffic jams, in social media, for monitoring places or in many other areas of society. A public scenario for the use of such technology is the delivery of public services or the maintenance and management of public infrastructure. The European strategy for data of the EU explains some of the examples of use: “Data is created by society and can serve to combat emergencies, such as floods and wildfires, to ensure that people can live longer and healthier lives, to improve public services, and to tackle environmental degradation and climate change, and, where necessary and proportionate, to ensure more efficient fight against crime” (EU COM 2020/66 final).
Personal Dimension
When talking about datafication we need to mention also the impact of these processes on the individuals. If personal identity is a construction, co-created by the creators and owners of (digitalised) artefacts and digital infrastructure, then also the digital self must be pre-structured through the principles and rules of computer mediation. (Chaudron & Eichinger, 2018). Users and platforms create not only personal data traces or data shadows, but also digital selves, the presence of individuals in the digital sphere which goes far beyond a mere extension of their analogue appearance.
The question for individual users is how they will manage it. Furthermore, these processes require individual data and in consequence users that are identifiable. The ongoing discussions on the risks and challenges related to biometry illustrate that identification is not only the basis for individualised and comfortable user experience but also a basis for inclusion – or exclusion of citizens from spaces or benefits. It raises also questions how anonymity and privacy can be granted in a digital-analogue environment. Conflicts regarding private and public surveillance are from this perspective necessarily accompanying ongoing digitalisation of our infrastructures and lives.
The omnipresence of technology and computer-mediated commuication is also affecting our self-perceptions and has impact on our competences. The reality perceived through a digital lens is appearing differently to the analogue reality. While people lernt in the earlier decades to differentiate between the appearance of the world in TV or newspapers and between their own life, they are today also part of the mediated reality. Also the availability of datafication for physical and behavioral tracking and analysis is a new challenge. Although the approach is not new, now the tzechnology is widespread and in use. Unreflected measuring, tracking and performance optimizing might influence our self-esteem grounded on the idea that human beings are by nature imperfect psycho-physical and social beings. Although most people find resilient strategies to cope with these challenges, not all are finding a healthy balance. Another issue seems to be connected to the growing human-machine interactions. Automatisation, robotics or AI managed systems are having an impact on human control and autonomy and let us start ethical debates about their control and limitation.
Many of theses aspects are tackling our „creepy line“, a term coined by Eric Schmitt: Google policy about a lot of these things „is to get right up to the creepy line but not cross it. Implanting things in your brain is beyond the creepy line. At least for the moment until the technology gets better“ (Schmidt, 2010). The creepy line is depending not only from the technology but also from its purpose and from trust in the people implementing and controlling this technology. In this sense, civil society and citizens should debate the scenarios for making use of technology close to our bodies and brains and give more attention to the pluralism of voices also outside the civil society. We can only influence their development if beyond a technic-centered prioritisation of the platforms also the priorities of users and citizens get access into the structured dialogue of pros and cons: „If it is right, that the civilised world is nothing than a (falsified) hypothesis, then it’s time today for the counter hypothesis“ (Beck, 1988, p. 27.
What are our Creepy Lines?
Our fears in regard to new developments – are a natural reminder not to go too far not to cross our creepy line. In this sense, they are helpful signals inducing us to reflect our needs and goals.On the other hand, critical thinking involves a reflection of these concerns and fears and their intellectual foundation.
What is acceptable? What is beyond the creepy line?
- Monitoring of the private space
- Processing of private data and sharing it with third state or other third parties
- Data analysis on the basis of individual profiles
- Non-invasive human-machine interaction
- Implants, prothesis
- Performance tracking through others (employer, partner, doctor, ...)
- ...
Smart Home
Beyond the smart mobile devices, the smart home should also be mentioned as a part of the environment of this Internet of Everything. It includes not only digital assistants, but the whole collection of digitalised technology in between our four walls. Currently in many countries, water, heating and electricity consumption is measured by smart meters. Manual documentation is not required anymore as the data is transmitted automatically to the supplier. As an added value, digitalisation allows better tracking and analysis. For instance, one can assess the consumption in much more detail than only once or twice a year in aggregated form.
In 2019, Google, Amazon, and Apple joined forces to establish a new standard for the Internet of Things: “Connected Home over IP”. In 2020, apps and devices for the monitoring and steering of light, heating and plug sockets appeared on the consumer market, as well as connected kitchen machines and fridges. Vacuum cleaners are drawing detailed ichnographies and storing them in a cloud. On average, each household has ten connected devices, but the tendency to adopt these tools is rising because of the availability of more available and affordable smart home technology (Bitdefender, 2016). More and more tablets, smartphones, TVs, consoles and eBook readers with smart features are complementing or replacing the desktop computer. Connected entertainment and data storage solutions are appearing in our households. Media servers (hard disks with internet access) are replacing spacious CD and DVD collections. Storage disks and network printers are, thanks to their connectivity, accessible for different users in our home network or even from outside our home, through the internet. Cameras are becoming connected to smartphones, PCs, or printers, over Wi-Fi or via memory cards with Wi-Fi modules.
Finally, the picture would not be complete if we did not mention the ”datafied” infrastructures outside our four walls. Sensors embedded in our public life measure pollution, noise, traffic and lead to improved management and maintenance of these infrastructures. But also personal information is collected and analysed, for instance by license plate or facial recognition. The combination of such infrastructural information with personal data is making new forms of ubiquitous computing imaginable. This is the narrative of the smart city. The discussion about smart infrastructure is oscillating between visions of horizontal and open data on the one side, and a commodification of public infrastructures through IT, often in private ownership on the other side.The more common they are, the more invisible and intuitive technology and processes become, with an ambivalent effect on people’s knowledge and awareness of them.
Stocktaking: Smart Home
Stocktaking can be a starting point for their control. On average, ten connected devices are part of each household.
- How many devices do you connect via your router or mobile?
- How many meters are digitized in your household?
Between 30% and 40% of users never updated firmware or initiated security updates.
- And you?
- Many people don’t know, how that would work. Do you?
You might control your router through a website (the user interface). For example, you might see how many devices are online and how much data volume you used and when. Here you might as well initiate updates and change passwords or set new accounts.
- Have you ever had a look into this backend?
- When did you update your router las
Platformisation
The birth myth of the internet was the promise of horizontal communication. In between it developed in a different directions. The new platforms’ power are strongly connected with the technological capacities and the processing approach of big data. Strong financial investors back these. From users perspective, intuitiveness of usage is too often connected with lacking overview or control. The ubiquitous network of servers, services and digital norms are co-structuring our social behaviour via platforms, apps, proprietary devices. Platformisation of the internet means according to Poell et al. The „penetration of the infrastructures, economic processes, and governmental frameworks of platforms in different spheres of life.“ And also shift our idea from the Internet since it can be also perceived as a „reorganisation of cultural practices and imaginations around platforms“ (Poell et al., 2019, p. 6).
Platformisation: Penetration of the infrastructures, economic processes, and governmental frameworks of platforms in different spheres of life. Reorganisation of cultural practices and imaginations around platforms (Poell et al., 2019, p. 6).
Conversely, those who have the technical possibilities and the algorithms are gaining influence. The platformisation of the internet was pushed by economic phantasy and taking financial risk. Venture capital caused a first dot-com bubble that burst around 2003. Soon the digital market grew further, surviving the economic crisis in 2008. Today, the most profitable public corporations are technology conglomerates. “In effect, digital platforms have become systemically important in the digital economy, similar to the financial sector itself” (Nogared & Støstad, 2020, p.7). The huge necessary investments are stimulated by an investor driven venture capitalism and also by massive direct or indirect state investments, for instance in security or surveillance technology (Zuboff, 2018, p. 113 ff.).
The underlying question in regard to our digital identities is how individuals might meet platforms and their creators at eye-level. Is the customer king? In particular, the platforms save with direct contact to their users. In consequence, platforms and their power are today becoming a focus of regulation debates. One aspect is the monopolistic tendencies with the domination of closed environments. Is Shohana Zuboff right, when she names the dominant way of designing data driven business models as „surveillance cpaitalism“ (Zuboff, 2018)?
Heterogenity and the decentral character of the internet is crucial for its further existence. The Mozilla Foundation is advocating for more competition and for the diversity: “A healthy balance of power in our global internet ecosystem depends on a delicate interplay between governments, companies and civil society. We need effective competition standards and technical interoperability – between the products of different companies – to ensure that the internet grows and evolves in ways that accommodate the diverse needs of people around the world“ (Mozilla Foundation, 2019, p. 98). Also the EU’s Next Generation Internet Initiative puts it in a similar way, by defining the challenge as “to shape the future internet as an interoperable platform ecosystem that embodies the values that Europe holds dear: openness, inclusivity, transparency, privacy, cooperation, and protection of data”(EU NGI, 2020). Aside platforms created a new way to organise work, especially the new „platform work“. They created new ways of production and cooperation and are shifting from the role of mediators or facilitators of services toward a third party in the triangle customer-client-platform. Platforms are setting the rules for their users. They are surveilling the working processes, analyse and collect performance data, nudge service providers actively and are directing them (Ivanova et. al., 2018, p. 7f). When the status of platform workers is shifting in between empoyment and self-employment, the platforms are shifting toward the role which in traditional working relations overtook entrepreneurs. „People who are deliberately kept in the dark about how the market works can hardly be considered entrepreneurs“ (Ivanova et al., 2018, p. 22).
Conclusions for Civic Education
Information and Overview
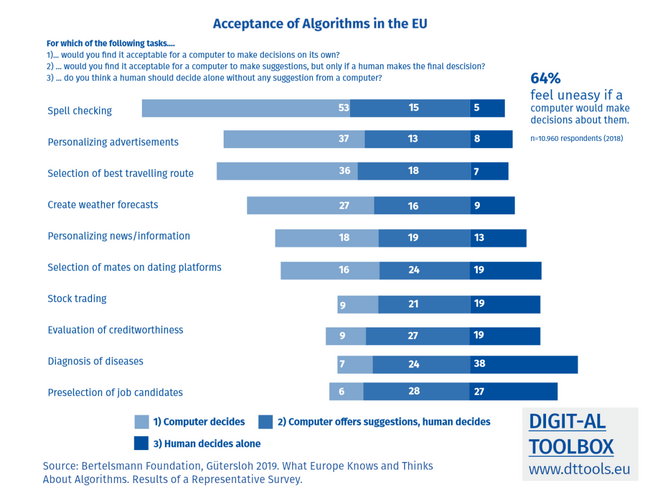
Ubiquitous computing is intuitive and becoming a matter of course. However, this comes with two challenges – information and overview. The more we take things for granted, the more we forget them or ignore the conditions necessary for their existence. Only when they don’t work, do we realize how dependent we are on them. Human Rights Education and Education for Active Citizenship can contribute to overview and information and raise awareness of learners about the concrete activities of the technology under the surface of the visible interaction.
This literacy would entail big data, AI and algorithm knowledge and also knowledge about the techno-social and data-economic models driving the transformation. These very different cultural, social, economic and political ideas are also inscribed in different political programs, personal attitudes, advocacy agendas and business models which might be explored.
Evolutionary Perspective
Also the evolutionary perspective might help learners to reflect developments and to explore their picture of future digitalisation. For instance, along their individual internet or technology biography: When did they get into touch with what kind of technology? What did they do then? What were key events in their lives? What has changed for them personally? Where were hopes and hypes, and also threats and disappointments? Where did their opinion change?
Individual Connectedness and Experience
Learners might raise awareness about their individual connectedness within the digital sphere. What kind of devices do they use? How do these interact, with whom? How do they work, or what do they know about them?
Since algorithmic computing and platforms rely on prod-users, users of platforms and producers of content or interaction in one person, nearly all adult learners have had experience with big data, artificial intelligence, scoring/rating or algorithmic selection or filtering. Where, and what kind of experience? A concrete individual reflection can be a motivational driver to enter learning about these abstract concepts and the technology, about rights and values in the digital sphere.
Rights
Also rights-centred learning neds more attention in order to asess risks and potentials of existing or future technology. This involves among others privacy in the narrow sense access to the digital sphere, ownership of data, or free speech , non-discrimination or free choice. In particular, we might ask, how processing in the frame of big data can get along with fundamental rights? A deeper exploration of the GDPR seems to be a good starting point for adult education.
Information about Data Processing
Information and consent are central issues that need also more awareness. Very often, consent is superficial, rather a formal consent expressed by a fast click on cryptic terms of service or privacy agreements. Education might bring light to this cryptic process. Close to the everyday experience of learners civic education might help: Once data is stored, analysed and shared, how can users then learn about their data traces? Where and how are they stored and for what purposes? What would make people factually exert control over their personal information?
Informed Choice
Beyond consent, this is a question of good choice. Alternative options must be known and must be available for use. Privacy protection starts also in the personal four walls.
Nils-Eyk Zimmermann
Editor of Competendo. He writes and works on the topics: active citizenship, civil society, digital transformation, non-formal and lifelong learning, capacity building. Coordinator of European projects, in example DIGIT-AL Digital Transformation in Adult Learning for Active Citizenship, DARE network.
Blogs here: Blog: Civil Resilience.
Email: nils.zimmermann@dare-network.eu
References
Illustration: Felix Kumpfe/Atelier Hurra
Beck, U. (1988). Gegengifte. Die organisierte Unverantwortlichkeit; Suhrkamp Verlag, Frankfurt
Chaudron, S.; Eichinger, H. (2018). Eagle_eye on – Identities in the digital world, Evolution and challenges. Joint Research Council (JRC), Publications Office of the European Union, Luxembourg. https://doi.org/10.2760/48837
European Commission (EU COM 2020/66 final). Communication from the Commission to the European Parliament, the Council, the European Ecopnomic and Social Commmittee and the Committee of the Regions. A European strategy for data. European Union (EU NGI 2020). Next Generation Internet Initiative. Abgerufen von: https://www.ngi.eu/.
Ivanova, M; Bronowicka, J.; Kocher, E.; Degner, A (2018). The App as a Boss? Control and Autonomy in Application-Based Management. Arbeit | Grenze | Fluss - Work in Progress interdisziplinärer Arbeitsforschung Nr. 2, Frankfurt (Oder), Viadrina. https://doi.org/10.11584/Arbeit-Grenze-Fluss.2
Mayer-Schönberger, V. (2015). Was ist Big Data? Zur Beschleunigung des menschlichen Erkenntnisprozesses. In: Aus Politik und Zeitgeschichte/bpb.de 6.3.2015, Beilage zur Zeitung „Das Parlament“ Bonn
Meidert, U.; Scheermesser, M.; Prieur, Y.; Hegyi, S.; Stockinger, K.; Eyyi, G.; Evers-Wölk, M.; Jacobs, M.; Oertel, B.; Becker, H. (2018). Quantified Self - Schnittstelle zwischen Lifestyle und Medizin. TA-SWISS 67, Zurich. https://doi.org/10.3218/3892-7
Mozilla Foundation (2019). Internet Health Report. Transcript Verlag, Bielefeld.
Nogared, J; Støstad, J-E (2020). A Progressive Approach to Digital Tech; Taking Charge of Europe’s Digital Future. FEPS – Foundation for European Progressive Studies, SAMAK – The Cooperation Committee of the Nordic Labour Movement. Brussels: 2020.
Poell, T. & Nieborg, D. & van Dijck, J. (2019). Platformisation. Internet Policy Review, 8(4). https://doi.org/10.14763/2019.4.1425
Schmidt, E. (2010). Eric Schmidt a t the Washington Ideas Forum in Washington, D.C. on October 1, 2010. (from 14:10)
Spiekermann, S. (2010). About the “Idea of Man” in System Design – An enlightened version of the Internet of Things? In Architecting The Internet of Things, edited by D. Uckelmann, M, Harrison, F. Michahelles, Springer Verlag, 2010, p. 25-34. http://ssrn.com/abstract=2046497
Weiser, M. (1991). The Computer for the 21st Century in: Scientific American 09/1991; 94-104.
Zuboff, S. (2018). The Age of Surveillance Capitalism. The Fight for a Human Future at the New Frontier of Power. Profile Books, London 2019.
Zuboff, S (2015). Big Other: Surveillance Capitalism and the Prospects of an Information Civilization (April 4, 2015). Journal of Information Technology (2015) 30, 75–89. https://doi.org/10.1057/jit.2015
The Digital Self
This text was published in the frame of the project DIGIT-AL - Digital Transformation Adult Learning for Active Citizenship.
Zimmermann, N. with Martínez, R. and Rapetti, E.: The Digital Self (2020). Part of the reader: Smart City, Smart Teaching: Understanding Digital Transformation in Teaching and Learning. DARE Blue Lines, Democracy and Human Rights Education in Europe, Brussels 2020.